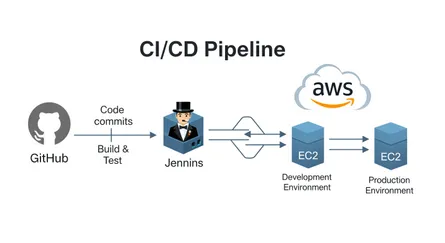
In today’s fast-paced DevOps environments, Infrastructure as Code (IaC) has become a cornerstone for managing and scaling infrastructure efficiently. Terraform, a leading open-source IaC tool, is widely adopted for its ability to automate infrastructure deployment across multiple cloud platforms. However, there’s often a question: What’s the best way to deploy Terraform configurations using CI/CD pipelines?
This blog will explore how Terraform fits into CI/CD workflows, how to deploy infrastructure using CI/CD pipelines, and answer key questions about integrating Terraform into your DevOps practices.
Is Terraform Good for CI/CD?
Absolutely, Terraform is an excellent tool for CI/CD pipelines because it allows teams to automate the entire infrastructure deployment lifecycle. It integrates seamlessly with various CI/CD tools and provides robust, reusable infrastructure modules.
The primary benefit of using Terraform in CI/CD pipelines is automation. Whether you’re managing a multi-cloud environment or a single platform, Terraform ensures your infrastructure is consistent, repeatable, and version-controlled.
Benefits of Terraform in CI/CD
- Consistency: Every infrastructure change is recorded and can be repeated with precision.
- Scalability: Terraform supports large-scale deployments, making it perfect for cloud-native architectures.
- Flexibility: It works across different cloud platforms (AWS, Azure, GCP), which means you don’t have to depend on provider-specific tools.
- Collaboration: By storing your infrastructure code in Git repositories, teams can collaborate, review, and approve infrastructure changes through pull requests.
FAQ: Why is Terraform particularly well-suited for CI/CD?
Terraform’s declarative syntax allows you to define your infrastructure, much like application code. When integrated with CI/CD pipelines, this makes it possible to deploy changes, enforce policy checks, and ensure compliance in a fully automated way.
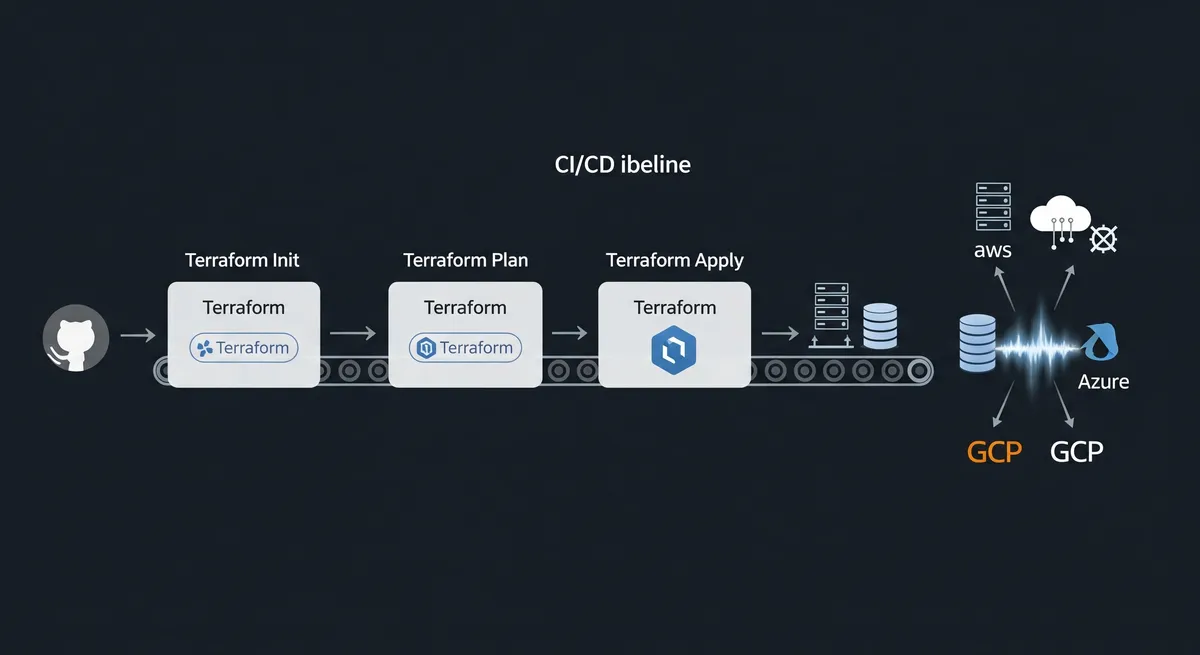
How Do You Deploy Your Infrastructure in CI/CD Using Terraform?
Terraform’s design philosophy makes it relatively simple to deploy infrastructure using any CI/CD system. Here’s a general approach to how you can do this:
Step 1: Write Your Terraform Code
Begin by writing the Terraform code that describes the infrastructure. Whether it’s provisioning servers, databases, or networking components, you define the desired state of your environment.
Step 2: Store Your Code in Version Control
Next, store your Terraform configurations in a version control system like GitHub or GitLab. This enables collaboration and ensures that changes to the infrastructure are reviewed and approved through pull requests.
Step 3: Automate the Workflow with a CI/CD Tool
Integrate a CI/CD tool such as Jenkins, GitLab CI, CircleCI, or GitHub Actions to automate the Terraform workflow. The CI/CD tool will perform the following tasks:
- Terraform Init: Initialize the Terraform environment.
- Terraform Plan: Show what changes will be made to the infrastructure.
- Terraform Apply: Apply the changes and update the infrastructure.
FAQ: How do CI/CD tools manage state in Terraform?
Terraform uses a state file to keep track of the current infrastructure. This state is crucial for Terraform to understand what exists in the real-world infrastructure versus what’s defined in code. Store the state file securely (e.g., using an S3 bucket or Terraform Cloud) so that CI/CD pipelines have access to the latest state during deployments.
Where Does Terraform Fit in DevOps?
Terraform is a critical tool in the DevOps toolkit because it bridges the gap between infrastructure and development pipelines. It allows developers to treat infrastructure as code, enabling them to provision and manage infrastructure through automated, repeatable processes.
Key Benefits in a DevOps Workflow:
- Continuous Delivery: Terraform works hand-in-hand with CI/CD pipelines, allowing for continuous delivery of infrastructure updates.
- Version Control: Infrastructure changes are tracked in the same version control system as application code, which makes rolling back to previous versions straightforward.
- Security and Compliance: Terraform allows you to enforce security policies through automation, ensuring your infrastructure meets compliance requirements.
FAQ: How does Terraform enhance collaboration in DevOps?
By integrating with CI/CD pipelines, Terraform enables teams to collaborate more effectively. Developers, operations, and security teams can review changes, apply policies, and ensure that infrastructure updates are safe and aligned with business needs—all without manual intervention.
How to Create a CI/CD Pipeline in GitHub Actions for Terraform?
One of the easiest ways to deploy Terraform using CI/CD is by leveraging GitHub Actions. GitHub Actions is a flexible CI/CD tool that allows you to automate workflows directly in your GitHub repository.
Here’s a step-by-step guide to creating a CI/CD pipeline in GitHub Actions for Terraform:
Step 1: Define a Workflow
In your GitHub repository, create a .github/workflows/main.yml file. This file defines the CI/CD pipeline.
name: Terraform Deployment
on: push: branches: - main
jobs: terraform: runs-on: ubuntu-latest
steps: - name: Checkout Code uses: actions/checkout@v2
- name: Set up Terraform uses: hashicorp/setup-terraform@v1 with: terraform_version: 1.0.0
- name: Terraform Init run: terraform init
- name: Terraform Plan run: terraform plan
- name: Terraform Apply run: terraform apply -auto-approveStep 2: Add Security and Secrets
In GitHub Actions, you’ll need to store sensitive data (like cloud provider credentials) securely using GitHub Secrets. This ensures that your pipeline can authenticate with the cloud provider without exposing credentials in the code.
Step 3: Trigger the Pipeline
The pipeline is triggered whenever changes are pushed to the main branch, automating the entire Terraform workflow from initialization to applying changes.
FAQ: Why use GitHub Actions for Terraform?
GitHub Actions is highly customizable and integrates natively with GitHub repositories, making it ideal for teams already using GitHub for source control. Its flexibility allows you to build, test, and deploy infrastructure with Terraform in a streamlined, automated way.
Best Practices for Terraform in CI/CD Pipelines
To get the most out of using Terraform in CI/CD pipelines, here are a few best practices to follow:
1. Use Remote State Storage
Store your Terraform state file in a remote backend (like an S3 bucket, Azure Blob, or Terraform Cloud) to ensure that CI/CD pipelines can always access the latest state. Remote state storage also prevents issues from multiple users or pipelines modifying the infrastructure simultaneously.
2. Perform Security and Compliance Checks
Use tools like Checkov or TFLint to scan your Terraform code for security vulnerabilities and best practices before applying it in production.
3. Test Infrastructure Changes in Staging
Before applying any changes to production, deploy the infrastructure in a staging environment. This ensures that any issues are caught early in the development lifecycle.
4. Automate Rollbacks
Always include a rollback strategy in your CI/CD pipeline. In the event of a failed deployment, your pipeline should automatically revert the infrastructure to the previous stable state.
Conclusion
Incorporating Terraform into your CI/CD pipeline is a no-brainer for teams looking to automate infrastructure deployments at scale. Whether you’re using GitHub Actions, Jenkins, or any other CI/CD platform, Terraform’s flexibility and cross-cloud compatibility make it a powerful tool in your DevOps arsenal. By following best practices and ensuring security and compliance checks are part of your process, you can confidently deploy infrastructure changes faster and more reliably.
References
- Terraform Documentation - HashiCorp.), https://www.terraform.io/docs
- GitHub Actions Documentation.), https://docs.github.com/en/actions
- Terraform Best Practices - HashiCorp Learn.), https://learn.hashicorp.com/collections/terraform/best-practices
- Using Terraform with CI/CD - HashiCorp Learn.), https://learn.hashicorp.com/tutorials/terraform/cicd-pipeline
- Infrastructure as Code - AWS Whitepapers.), https://aws.amazon.com/whitepapers/?whitepapers-main.sort-by=item.additionalFields.sortDate&whitepapers-main.sort-order=desc&awsf.whitepapers-content-type=*all&awsf.whitepapers-global-methodology=*all&awsf.whitepapers-tech-category=tech-categories%23devops (Search for “Infrastructure as Code”)
- Terraform State Management - HashiCorp.), https://www.terraform.io/docs/language/state/index.html
- Checkov - Bridgecrew by Prisma Cloud.), https://www.checkov.io/
- TFLint - Terraform Linter.), https://github.com/terraform-linters/tflint
- “Continuous Delivery with Terraform and GitHub Actions” - (Example: Blog post from a reputable tech blog like Medium, DEV.to, or a company blog.), [Link to a relevant blog post]
- “Automating Terraform Deployments with GitLab CI” - (Example: GitLab documentation or a community tutorial.), [Link to a relevant resource]
- “Best Practices for Managing Terraform in a Team” - (Example: Article from Gruntwork or similar IaC focused company.), [Link to a relevant article]
- “Securing Your IaC Pipeline” - (Example: Article from a cloud security vendor or a security-focused blog.), [Link to a relevant resource]