The cloud journey often kicks off with a single AWS account – it feels simple and straightforward, especially when you’re just starting out or have smaller teams. But as your cloud usage grows, that initial simplicity can turn into a bit of a tangled web. Suddenly, you’re juggling permissions for tons of users and services, trying to keep track of costs for different projects, making sure everything is secure, and figuring out those AWS service limits. This is where thinking about a multi-account AWS architecture becomes really important. By smartly dividing your work and resources into separate, self-contained AWS accounts, you can build a much stronger and easier-to-manage cloud setup. And to make governing all those accounts even simpler, AWS offers a fantastic service called Control Tower.
Why Should You Think About a Multi-Account AWS Architecture?
So, why bother with a multi-account setup for your AWS environment? Well, the main idea is to keep different types of work and resources in their own separate AWS accounts. This separation gives you a bunch of really helpful advantages that make dealing with a large cloud environment much easier than trying to cram everything into one account.
One of the biggest pluses is better security. Think of separate accounts as strong, natural walls. By default, what’s in one account can’t be touched by another, which acts as a built-in safeguard against unauthorized access or accidental mistakes. This significantly limits the damage if something does go wrong in one area. If one account gets compromised, it usually stays contained, preventing the problem from spreading to your other important work or sensitive information in different accounts. Plus, a multi-account approach lets you set up different security measures that are just right for each specific environment. For example, what you need for your development environment is probably very different from what you need for your live production systems. Separate accounts let you apply the right security rules to each. Some companies even have a central security account just for keeping an eye on and sending alerts for all their other accounts, giving them a bird’s-eye view of their security. This built-in isolation that comes with having multiple accounts creates a really solid foundation for your security, making it much harder for a problem in one place to mess up your whole cloud setup.
Meeting compliance requirements also becomes much easier with a multi-account strategy. Putting sensitive work or data into its own dedicated accounts simplifies the whole process of proving you’re meeting regulations. For instance, if you need to follow rules like the Payment Card Industry Data Security Standard (PCI DSS) or the General Data Protection Regulation (GDPR), keeping the relevant stuff in a specific account makes it much simpler to show auditors that you’re doing things right. This detailed control over compliance within individual accounts helps organizations meet different rules for different types of data and work more effectively.
Keeping track of costs also gets clearer and more efficient with a multi-account architecture. Each account naturally becomes a way to separate and track spending. You can easily see exactly how much each account is costing, making it simpler to assign expenses to specific teams, projects, or clients. This better view of where your money is going helps teams make smarter choices about how they use resources and design their systems. While AWS Organizations lets you combine billing for an overall view, having that fundamental cost separation at the account level gives you much more detailed financial control and accountability.
From a day-to-day operations perspective, a multi-account approach leads to better organization. Separating work based on its purpose or environment, like having different accounts for development, testing, and your live production systems, improves overall organization and reduces the risk of accidentally messing things up between different teams or projects. Different parts of your business or different product teams often have their own ways of doing things and their own security needs. Separate accounts allow them to have more control while still following the company’s main rules. This separation of environments also means that changes or problems in one area are less likely to affect others, making things more stable and allowing for more flexibility.
Finally, a multi-account strategy helps you manage service quotas more effectively. AWS service quotas are the maximum number of resources you can have in your account, and these limits apply to each account separately. By spreading your work across multiple accounts, you can essentially increase your overall ability to use resources without hitting the limits of a single account. This stops different projects from competing for the same quotas and allows you to scale more easily as your cloud usage grows.
What Exactly is AWS Control Tower and How Does It Make Things Easier?
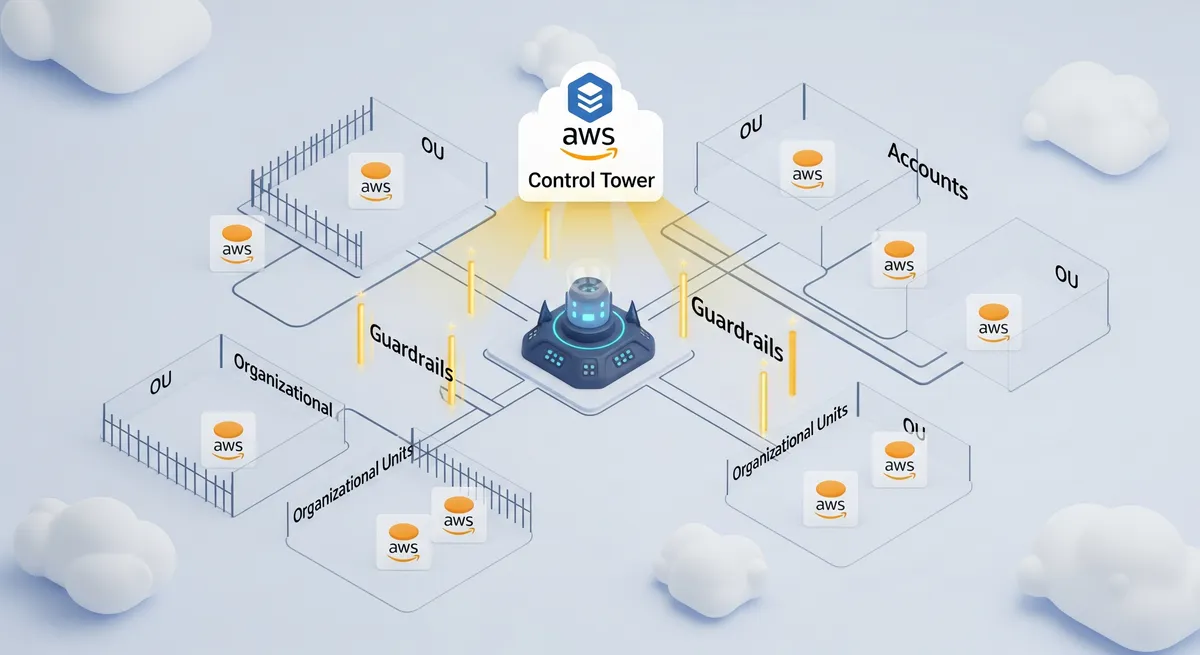
So, how does AWS Control Tower simplify managing all these accounts? Well, Control Tower is a service that’s designed to automatically set up and govern a secure multi-account AWS environment. It does this by creating what’s called a “Landing Zone,” which is basically a well-thought-out, multi-account foundation built on AWS best practices. Control Tower works behind the scenes with several other AWS services, like AWS Organizations, AWS Service Catalog, and AWS IAM Identity Center, to give you a smooth and automated experience.
One of the biggest advantages of Control Tower is its automated Landing Zone setup. It takes care of creating that initial multi-account environment for you, including setting up AWS Organizations, creating those essential first accounts (like the main management account, an audit account, and a log archive account), and organizing them into logical groups called organizational units (OUs). This whole process can take less than 30 minutes which is a huge time-saver compared to manually setting up everything yourself. This automation helps you get started with your cloud adoption faster and reduces the chance of making mistakes during the initial setup.
AWS Control Tower also gives you an “Account Factory,” which is a standardized and automated way to create new AWS accounts within your Control Tower environment. Using pre-defined account templates, the Account Factory makes sure that all new accounts are created with the right settings, ensuring consistency and compliance right from the start. This helps your organization stick to its rules and security requirements across all your accounts.
Another really important feature of AWS Control Tower is its Comprehensive Controls Management, often called guardrails. These are pre-built governance rules for security, how you operate things, and compliance. You can apply these rules across your entire organization or to specific groups of accounts. These controls can either stop bad things from happening in the first place (preventive) or monitor and record activities to make sure you’re staying compliant (detective). These guardrails help find and fix potential security problems, keeping your AWS environment secure and compliant. This proactive and reactive governance helps maintain a strong security and compliance stance across all your accounts, preventing rule violations and spotting any issues.
AWS Control Tower also provides a centralized dashboard that gives you a constant overview of your entire multi-account environment. This dashboard shows you all the accounts you’ve set up, the controls you’ve enabled, and any resources that aren’t following the rules. Having this single place to see the health and compliance of your multi-account setup makes monitoring and managing things much simpler for administrators.
Finally, AWS Control Tower works seamlessly with other key AWS services. It’s built on top of AWS Organizations for managing accounts and enforcing policies, uses AWS Service Catalog for creating new accounts through the Account Factory, and often integrates with AWS IAM Identity Center (formerly AWS SSO) for managing identities and access in one place. This integration makes it easier to use these different services together, giving you a smooth and efficient way to manage your multi-account AWS environment.
Landing Zones: Your Foundation for a Secure Setup
What exactly is a Landing Zone, and why is it so important when you’re using Control Tower to manage a multi-account AWS setup? A Landing Zone is essentially a well-designed multi-account AWS environment that’s built with security and compliance best practices in mind. AWS Control Tower automates the creation of this foundational environment for you. Think of it as the initial blueprint and infrastructure that gives you a secure and scalable starting point for your organization’s journey in the cloud.
A typical Landing Zone includes several key parts. At its heart is AWS Organizations, which provides the structure for managing all your AWS accounts from one place and applying company-wide rules. Within Organizations, accounts are grouped into Organizational Units (OUs) based on what they’re used for or what environment they belong to. Common OUs often include a Security OU for security-related accounts and tools, and a Sandbox OU for development and testing. The Landing Zone also sets up essential shared accounts, usually including a management account for overall administration, an audit account for keeping centralized logs from AWS CloudTrail and AWS Config, and a log archive account for securely storing these logs. For managing who can access what across all these accounts, the Landing Zone often uses Identity and Access Management (IAM), frequently along with AWS IAM Identity Center for managing users and their access in one place. While Control Tower provides the basic networking setup, you’ll still need to figure out your specific cross-account networking strategies. Finally, the Landing Zone comes with an initial set of security and compliance controls (guardrails) that are applied to the OUs or individual accounts. The way you structure your OUs within the Landing Zone is really important because it gives you a logical way to apply your governance policies effectively. Overall, the Landing Zone provides a consistent and repeatable foundation for deploying your applications and workloads in a multi-account environment, making sure you have good security and compliance right from the start.
Boosting Security and Making Sure You’re Compliant with Control Tower
How exactly does Control Tower make your multi-account AWS environment more secure and compliant? As we mentioned earlier, the key to Control Tower’s governance is its preventive and detective controls, also known as guardrails. These controls are designed to automatically enforce your organization’s rules and best practices.
For example, some security-focused controls might include requiring multi-factor authentication (MFA) for the main root users to protect your primary account credentials. Another important control could be to prevent public read access to your Amazon S3 buckets, stopping accidental data leaks. Making sure that AWS CloudTrail is turned on in all your accounts is another common security control, as it gives you a record of all actions taken within your AWS environment. You can also set up controls to stop people from creating resources in AWS Regions that you haven’t approved, which can limit your attack surface and potentially save you money.
When it comes to compliance, Control Tower offers controls to enforce specific encryption standards for your data, both when it’s stored and when it’s being transferred. It can also help restrict access to sensitive data to only the accounts and users who are authorized. Furthermore, Control Tower provides managed controls that are designed to help organizations meet digital sovereignty requirements related to where their data is stored, how access is restricted, encryption, and how resilient their systems are. Control Tower also works with AWS Security Hub, a service that gives you a comprehensive view of your security across all your AWS accounts, further improving security monitoring and checks against best practices. The ability to see all your security monitoring and alerts in one place through services like Security Hub, as mentioned in the research, gives you a unified way to respond to incidents and manage your security continuously. The automated governance that Control Tower’s controls provide helps organizations follow both their own internal security rules and external regulations, significantly reducing the risk of security breaches and compliance issues. The flexibility to choose and apply these controls at the OU level means you can implement security and compliance policies that are specifically tailored to the needs and risk levels of different types of work or teams.
Setting Up and Managing Your Multi-Account Environment: Practical Steps and Best Practices
What are the key steps and best ways to set up and manage a multi-account environment using AWS Control Tower? The initial setup of AWS Control Tower involves a few main steps. First, you need to make sure you have everything ready, like having an AWS Organizations setup and choosing your main AWS Region. Then, you can start the AWS Control Tower setup process from the AWS Management Console. When you’re setting up your Landing Zone, you’ll need to pick the AWS Regions you want to govern, enter email addresses for your shared accounts (management, audit, and log archive), and decide on your initial organizational unit (OU) structure. Control Tower will then automatically create those initial shared accounts for you. Once your Landing Zone is up and running, you can define and apply the security and compliance rules (guardrails) that fit your organization’s needs. To create new accounts within your governed environment, you’ll use the Account Factory, which provides a consistent process based on pre-set templates. If you already have AWS accounts, you can also enroll them into your Control Tower Landing Zone to bring them under the same management.
For managing things on an ongoing basis, there are several best practices to follow. Having a well-thought-out OU structure that matches your organization’s structure and needs is really important for applying policies and managing resources effectively. Using a consistent tagging strategy across all your accounts is essential for accurately tracking costs, automating tasks, and managing resources efficiently. It’s also important to regularly review and update your controls to make sure they’re still relevant to the latest security threats and compliance requirements. You should also keep an eye on the Control Tower dashboard to see the compliance status of your accounts and find any resources that aren’t following the rules. Clearly defining who is responsible for managing different parts of the multi-account environment is also key for smooth operations. Automating account creation and other management tasks whenever possible can make things more efficient and reduce the chance of human error. For organizations that need more advanced customization, exploring AWS Control Tower Account Factory for Terraform (AFT) can give you more flexibility in how you create and manage accounts. A well-planned setup, along with consistent monitoring and following these best practices, is essential for getting the most out of a multi-account AWS architecture managed by Control Tower.
Navigating the Landscape: Account Structure, Networking, and Identity Management
How do important architectural aspects like account structure, networking, and identity management fit into a Control Tower-managed multi-account environment?
Account Structure within a Control Tower environment is all about using Organizational Units (OUs) effectively to group accounts logically. Common ways to organize OUs include grouping accounts by environment (like development, testing, and production), by business unit, or by the type of work they handle. On top of this, the core shared accounts that Control Tower sets up for you – the management account, audit account, and log archive account – form the basic structure. A well-thought-out account structure, making good use of OUs, provides a clear and logical way to apply governance rules and manage resources as you grow.
Networking in a multi-account environment managed by Control Tower needs careful planning. While Control Tower sets up a basic framework, you’ll need to figure out how to enable secure communication and sharing of resources between different accounts. Options like VPC peering, AWS Transit Gateway, and AWS PrivateLink can be used to allow secure cross-account communication while still keeping the necessary security boundaries. Effective cross-account networking is crucial for allowing different teams and workloads in separate accounts to work together and integrate.
Identity Management in a Control Tower environment often uses AWS IAM Identity Center (formerly AWS SSO) to centrally control who can access what across multiple accounts. This gives you the benefit of single sign-on and makes managing users easier across your entire multi-account setup. Following the principle of least privilege, giving users only the permissions they absolutely need to do their jobs, is really important in a multi-account environment. You can achieve this by using IAM policies within individual accounts and Service Control Policies (SCPs) that you apply at the AWS Organizations level. Centralized identity management simplifies how users get access and allows you to apply security policies consistently across your whole multi-account landscape.
Frequently Asked Questions (FAQ) About Multi-Account AWS with Control Tower
AWS Organizations is the foundational service that lets you manage multiple AWS accounts from one place, offering features like combined billing and the ability to apply policy-based controls (Service Control Policies or SCPs) across your accounts. AWS Control Tower builds on top of AWS Organizations by giving you an automated and guided way to set up and govern a secure multi-account AWS environment. It creates a Landing Zone based on best practices, offers an Account Factory for easily creating new accounts, and provides pre-built controls (guardrails) for security, operations, and compliance. Think of Control Tower as simplifying and automating many of the tasks involved in setting up and managing a multi-account environment using Organizations.
Nope, there’s no additional charge for using AWS Control Tower itself. You only pay for the underlying AWS services that Control Tower sets up and manages for you, like the resources in your individual AWS accounts, AWS Organizations, AWS Service Catalog, and AWS IAM Identity Center.
Yes, AWS Control Tower lets you enroll your existing AWS accounts into your Control Tower Landing Zone. This means you can bring your current accounts under the same management and security policies that Control Tower provides.
While AWS Control Tower gives you a structured approach based on best practices, it also has options for customization. AWS Control Tower Account Factory for Terraform (AFT) allows for more advanced customization of how you create new accounts using code. You can also create your own custom controls to meet specific needs that go beyond the pre-built guardrails.
AWS Control Tower helps with compliance by providing those preventive and detective controls (guardrails) that automatically enforce your compliance rules across your multi-account environment. You can apply these controls at the organizational unit (OU) level to tailor compliance requirements to specific groups of accounts. Plus, it works with services like AWS Security Hub to continuously monitor and help you spot any areas where you might not be meeting your desired compliance standards.
You should consider moving to a multi-account setup with AWS Control Tower when your AWS usage starts to grow and you have different teams or types of work that have different security, compliance, or operational needs. It’s also a good idea if you need better ways to separate and see your costs, if you need strong security boundaries, or if you want to improve your overall management and security in the cloud. Even smaller organizations can benefit from the organized and secure approach that a multi-account strategy with Control Tower provides.
Conclusion: Embrace the Power of Multi-Account AWS with Control Tower
Moving to a multi-account AWS architecture offers some really significant advantages for organizations that want to build a secure, scalable, and well-managed cloud environment. You get better security by keeping things isolated, compliance becomes simpler by separating different types of work, managing costs is easier with clear breakdowns, operations run more smoothly by having separate environments, and you can handle service limits more effectively as you grow. AWS Control Tower makes setting up and managing this kind of environment much easier. Its automated Landing Zone setup, standardized Account Factory, comprehensive controls, and central dashboard give you a powerful set of tools for effectively managing multiple AWS accounts. By using AWS Control Tower, organizations can confidently handle the complexities of cloud growth, maintain strong security and compliance, and ultimately focus on innovating and delivering value to their customers. If you’re serious about building a robust and future-proof AWS infrastructure, exploring AWS Control Tower is a crucial step.
References
- Build an AWS Multi-Account Strategy According to Best Practices - Spacelift, accessed on April 6, 2025, https://spacelift.io/blog/aws-multi-account-strategy
- Benefits of using multiple AWS accounts - AWS Documentation, accessed on April 6, 2025, https://docs.aws.amazon.com/accounts/latest/reference/welcome-multiple-accounts.html
- Organizing Your AWS Environment Using Multiple Accounts, accessed on April 6, 2025, https://docs.aws.amazon.com/whitepapers/latest/organizing-your-aws-environment/organizing-your-aws-environment.html
- Benefits of using multiple AWS accounts - Organizing Your AWS Environment Using Multiple Accounts - AWS Documentation, accessed on April 6, 2025, https://docs.aws.amazon.com/whitepapers/latest/organizing-your-aws-environment/benefits-of-using-multiple-aws-accounts.html
- AWS multi-account strategy for your AWS Control Tower landing zone - AWS Documentation, accessed on April 6, 2025, https://docs.aws.amazon.com/controltower/latest/userguide/aws-multi-account-landing-zone.html
- Multi-account strategy for small and medium businesses | AWS Cloud Operations Blog, accessed on April 6, 2025, https://aws.amazon.com/blogs/mt/multi-account-strategy-for-small-and-medium-businesses/
- AWS Control Tower FAQs - Amazon Web Services, accessed on April 6, 2025, https://aws.amazon.com/controltower/faqs/
- What is AWS Control Tower? - nOps, accessed on April 6, 2025, https://www.nops.io/glossary/what-is-aws-control-tower/
- AWS Control Tower - AWS Documentation, accessed on April 6, 2025, https://docs.aws.amazon.com/controltower/latest/userguide/what-is-control-tower.html
- Cloud Security Governance - AWS Control Tower, accessed on April 6, 2025, https://aws.amazon.com/controltower/
- AWS Control Tower Features, accessed on April 6, 2025, https://aws.amazon.com/controltower/features/
- AWS Control Tower and AWS Organizations, accessed on April 6, 2025, https://docs.aws.amazon.com/organizations/latest/userguide/services-that-can-integrate-CTower.html
- Manage Accounts Through AWS Organizations - AWS Control Tower - AWS Documentation, accessed on April 6, 2025, https://docs.aws.amazon.com/controltower/latest/userguide/organizations.html