Think about how much stuff modern organizations have running in the cloud these days. It’s a lot, right? All those servers, applications, and connections can get pretty complicated to manage. Just clicking around in a console or trying to keep track of everything in spreadsheets? That doesn’t really cut it anymore if you want to stay secure, meet your compliance rules, and generally keep things under control. That’s where this idea of “policy as code” comes in. It’s a way of saying, “Hey, let’s use code to define and manage the rules that govern our tech stuff.” And one of the coolest tools out there for this is the Open Policy Agent, or OPA for short. It’s like a universal rulebook that can help you bring order to all sorts of different environments.
What Exactly is Policy as Code, and Why Should You Care?
Okay, so what’s the big deal with policy as code? Well, instead of having your important rules locked away in documents or spreadsheets that people might forget about or misinterpret, policy as code means you write those rules down in a way that computers can understand – as actual code. Think of it like this: you’re taking the guidelines for how your systems should behave and turning them into something like JSON or YAML files that software can read and act on. This is a huge step up from the old way of doing things, where you relied on people to manually check stuff, which, let’s be honest, can lead to mistakes. When you treat your policies like real code, you can use all the same smart techniques that developers use to make sure their software is reliable and efficient.
Policy as code works because it follows some pretty smart principles. First off, it uses a declarative language. That just means you describe what you want the end result to be, not the step-by-step instructions on how to get there. This makes your policies much clearer and easier to write because you’re focusing on the goal. Second, because it’s machine-readable, your policies can easily talk to different systems and tools, making automation a breeze. Third, just like with regular code, you can use version control to keep track of changes, see who did what, and work together with your team. And finally, automation is key. Your systems can automatically enforce these policies, so you don’t have to rely on manual checks, which makes everything much more consistent. Put it all together, and you’ve got policies that are clear, consistent, auditable, and enforced without a ton of manual effort.
Why should you actually care about all this? Well, the benefits are pretty awesome. You get more automation and consistency, which means your systems behave more predictably. You also get better security and compliance because you’ve got automated checks constantly making sure you’re following the rules. This also leads to faster and safer software releases because your policies are baked right into the development process. Compared to doing things by hand, policy as code is way more efficient, faster, gives you better visibility, improves collaboration, and is more accurate. Being able to see how policies have changed over time and having automated testing in place makes everything much more solid. Ultimately, by automating how you manage your policies, you can seriously cut down on human errors and keep your environments much more stable and secure.
Meet OPA: Your Unified Policy Engine for the Cloud
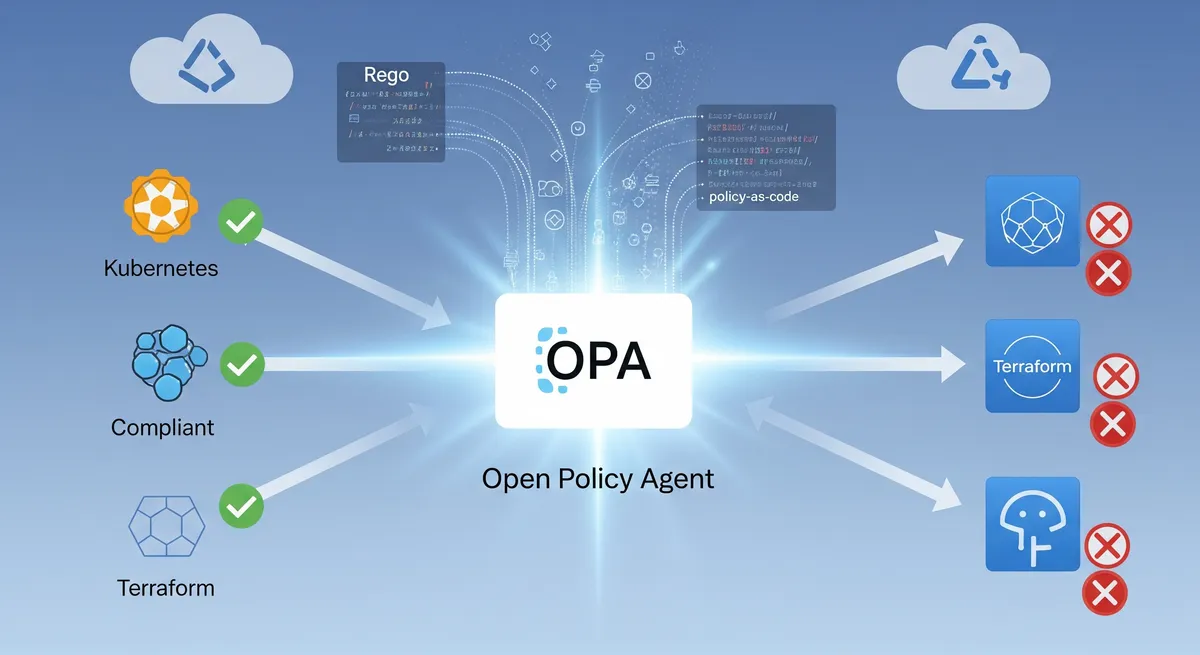
When it comes to policy as code, the Open Policy Agent (OPA) is a real standout. People often just call it “Oh-pa.” It’s an open-source tool that’s designed to be a single place to manage all your policies, no matter what part of your tech stack they apply to. It’s even a graduate of the Cloud Native Computing Foundation (CNCF), which means it’s a well-trusted and reliable piece of tech for managing policies in today’s cloud world. Because OPA can work across so many different services and platforms, it’s super helpful for organizations that want a consistent way to handle policies, making things less complicated and easier to govern.
OPA works by doing something really smart: it separates the decision of whether something is allowed from actually enforcing that decision. When a system needs to know if an action should be permitted, it sends input to OPA as structured data, usually in JSON format. Then, OPA takes that input and checks it against the policies you’ve defined, which are written in its special language called Rego. This involves a query based on the input and your policies, and OPA spits out an output that says what the policy decision is. Rego itself is based on simple if-then logic, so you can create rules that clearly state when something is allowed or not. Plus, OPA has a REST API that lets you manage your policies and ask for policy decisions, making it easy to connect with all sorts of systems and applications. This separation means that developers can focus on building their apps, while security and operations teams can handle the policies independently. And because Rego is declarative, it’s easier to just say what you want to achieve with your policies.
OPA’s brain, its architecture, has a few key parts that work together to figure out if a policy is being followed. The Policy Engine (OPA Core) is the main processor. It takes your policy questions and compares them to the policies and data you’ve loaded in. Rego, that special Policy Language, gives you a clear way to write down your policy rules. Input Data, usually in JSON, gives the engine the context it needs to make a decision. Policies, written in Rego, are where you put your specific rules and logic. And finally, the Policy Decisions (Output) are what OPA tells you – whether something is allowed or denied, or maybe some other useful information based on your policies. Understanding these pieces is super important if you want to use OPA effectively in your tech setup.
How Does Policy as Code with OPA Bolster Your Compliance, Security, and Governance?
Using policy as code with OPA can really help you get a better handle on three crucial things: compliance, security, and governance.
When it comes to compliance, OPA can automatically check if you’re meeting various regulations like GDPR, HIPAA, and PCI DSS. You just write these requirements as Rego policies, and OPA can constantly monitor and make sure you’re following them, which lowers the risk of getting into trouble. OPA can even create reports in real-time that show you which systems aren’t compliant and tell you exactly which policies they’re breaking. Plus, it keeps audit logs of all the policy enforcement, so you know who did what and when, which makes compliance audits much easier and gives you proof that you’re doing things right. This automation of compliance stuff saves a ton of time and effort compared to manual checks, helping you stay on the right side of the law and industry standards.
From a security standpoint, policy as code with OPA lets you proactively enforce security best practices. This includes things like making sure people only have the minimum access they need, setting up network boundaries, and making sure data is encrypted. You can also set up OPA to prevent risky things from being deployed, like unapproved software or container images from unknown sources. You can even limit access to resources based on things like the time of day, where someone is located, or their job role. By writing your security rules as code, you can automatically enforce them across your entire infrastructure and applications, making it harder for bad guys to get in and reducing the chances of security breaches. This proactive approach really beefs up your overall security.
In the world of governance, OPA makes it easier to use modern ways of developing and running software like DevOps, DevSecOps, and GitOps. By putting your policies into a clear, computer-readable format, OPA makes sure your policies are consistent across everything, from your infrastructure to your applications. You can even use it to keep costs down by setting limits on how much you spend on cloud resources and getting alerts or even stopping deployments that go over budget. OPA also helps with governance by checking if configuration changes and new deployments follow your rules before they even happen. This helps prevent mistakes and makes sure everything aligns with your organization’s standards. Finally, policy as code with OPA helps clarify who owns and is responsible for policies because they’re explicitly defined and managed as code, making it easier to know who to talk to if something needs to be changed. This unified and automated way of managing policies gives you better visibility and control, leading to more effective governance across your organization.
Policy as Code in Action: Integrating OPA with Terraform for Infrastructure Governance
The idea of policy as code really shines when you combine OPA with tools like Terraform that let you manage your infrastructure as code. Terraform lets you define and set up your infrastructure using code, and when you add OPA to the mix, you can enforce your policies right within your infrastructure workflows. This is super useful because it means you can check if your infrastructure changes are okay before they’re even made, catching any compliance or security problems early on. By governing your infrastructure deployments proactively, you can stop non-compliant resources from being created in the first place, leading to more secure and well-managed environments.
The typical process of using OPA with Terraform involves a few key steps. First, Terraform creates a plan as a JSON file, which shows all the changes it’s going to make to your infrastructure. Then, you write OPA policies in Rego to look at this plan and decide if it meets your rules. You can then use the OPA command-line tool or a special Terraform integration to compare the plan against your policies. Based on what OPA says (either “go ahead” or “stop”), you can then either apply the Terraform plan or hold off and fix any policy violations. This makes sure that all your infrastructure changes are checked against your rules before they’re actually put in place, making everything more consistent and reducing the risk of mistakes. The fact that the Terraform plan is in JSON format makes it easy for OPA to look at all the details of each resource and enforce policies based on those details.
Here’s a simple example of a Rego policy you could use with Terraform to make sure all your AWS resources have certain tags:
package terraform.checks
# Define the tags we absolutely needrequired_tags := {"environment", "project", "owner"}
# If an AWS resource is missing a required tag, say nodeny contains msg if { resource := input.resource_changes[_] resource.type == "aws_instance" or resource.type == "aws_s3_bucket" # Add other AWS resource types here missing_tag := required_tags - object.get(resource.change.after.tags, _) count(missing_tag) > 0
msg := sprintf("Resource '%s' is missing these required tags: %v", [resource.address, missing_tag])}This policy looks at all the changes Terraform is planning to make. For any aws_instance or aws_s3_bucket (you can add other types too), it checks if the tags that are supposed to be there after the change include all the tags in our required_tags list. If any are missing, it creates a message saying which resource is missing which tags and denies the change.
There are tons of other ways you can use OPA with Terraform. For example, you could restrict SSH access to your public servers to only allow connections from specific, approved IP addresses. You could also make sure that all your S3 buckets have encryption enabled before they’re created, keeping your data safe. And you could even limit the types of servers or cloud providers you’re allowed to use to help control costs or stick to company standards. These are just a few examples of how flexible and powerful OPA can be when it comes to enforcing infrastructure policies with Terraform.
Governing Your Container Orchestration: Leveraging OPA with Kubernetes
Policy as code with OPA isn’t just for infrastructure; it also works great with container platforms like Kubernetes, giving you a strong way to manage these dynamic environments. You can use OPA as a Kubernetes admission controller, which basically means it intercepts requests to the Kubernetes API server and checks if they follow your rules before letting them create or update things. A popular tool that makes this easier is OPA Gatekeeper. It’s a special Kubernetes component that helps you define and enforce these policies. By using OPA in this way, you can make sure your Kubernetes clusters are following security, compliance, and operational best practices.
OPA can do a lot of cool things within Kubernetes to help with governance. You can set policies to require resource limits (like CPU and memory) for all your containers, making sure you’re using your resources efficiently and preventing any one container from hogging everything. Another important use case is only allowing images from trusted registries, which helps protect you from deploying containers with known security problems. OPA can also make sure you have mandatory labels on your Kubernetes resources like namespaces, deployments, and pods, which is really helpful for organizing things, tracking costs, and enforcing policies based on specific attributes. You can even define policies to restrict the use of privileged containers, which improves your cluster’s security by limiting what those containers can do. OPA can also help you control network policies and how services talk to each other, ensuring that only authorized communication happens within your Kubernetes environment. These are just some of the ways OPA can help you enforce governance in Kubernetes.
The typical workflow for using OPA with Kubernetes involves first installing OPA Gatekeeper into your Kubernetes cluster. Then, you define your policies as Constraint Templates, which are written in Rego, and configure them using Constraints, which are special Kubernetes resources. When someone tries to create or change something in Kubernetes, the Kubernetes API server sends a request to OPA Gatekeeper. OPA then checks this request against the policies you’ve defined. Finally, OPA Gatekeeper tells the Kubernetes API server whether to allow or deny the request, and Kubernetes enforces that decision. This smooth integration makes sure that every change in your Kubernetes cluster is validated against your governance rules, leading to a more secure and compliant setup.
Navigating the Hurdles: Common Challenges and Solutions in Implementing OPA for Policy as Code
While using policy as code with OPA has a lot of advantages, you might run into some challenges when you’re first getting started. One common issue is the complexity of adopting a whole new way of thinking and getting it to work with your existing systems. Learning Rego, OPA’s policy language, can also be a bit of a curve, especially if your team isn’t used to declarative programming. Plus, it often requires a shift in how your teams work, as they need to get used to defining and enforcing policies in a new way. If you’re a big company with lots of different technologies, managing all those different systems and getting them to work with OPA can be tricky. Meeting strict audit and compliance requirements often means you need a really good understanding of both the regulations and what OPA can do. Making sure OPA runs efficiently and can handle a large scale in complex environments can also be a challenge. And if your policies aren’t written and tested well, they could even introduce new security problems. Keeping track of and managing the different versions of your policies across your infrastructure is another thing you’ll need to figure out. Lastly, the open-source version of OPA doesn’t have a lot of built-in tools for monitoring and managing it, which can make it harder to use at a large scale.
To get past these challenges, there are several things you can do. It’s really important to start with clear goals for your policies and to design them in a modular way, breaking down big, complicated policies into smaller, easier-to-manage pieces. You should also treat your Rego policies like any other code, using version control, testing them thoroughly, and integrating them into your CI/CD pipelines to make sure they’re reliable. Using well-defined permission models and keeping your policy code separate from your application code can also make things more secure and easier to manage. Separating the structure of your data from the actual data in your policies can also make them clearer. Making sure the OPA agent itself is secure through proper setup and access controls is also crucial. You might also want to look at using higher-level tools or interfaces that make it easier to write Rego policies. Using centralized policy management solutions, like Styra DAS, can help with distributing policies, monitoring them, and governing them at scale. Setting up clear rules and standards for your policies and encouraging collaboration and knowledge sharing among your teams are also key to making this work. And finally, you should log and monitor how your policies are being enforced and regularly review and update them to make sure they’re still effective. Overcoming these challenges takes a comprehensive approach that includes technical best practices, changes in how your organization works, and maybe even using some specialized tools.
To give you a better idea of what tools are out there for policy as code, here’s a quick comparison of some popular options:
| Tool | Description | Strengths | Weaknesses |
|---|---|---|---|
| Open Policy Agent (OPA) | General-purpose policy engine | Customizable, supports multiple languages | Can have a steeper learning curve |
| HashiCorp Sentinel | Policy as Code framework | Easy to use, works well with Terraform | Less flexible in terms of customization |
| AWS Config Rules | Policy evaluation for AWS services | Integrates seamlessly with AWS | Primarily focused on AWS environments |
| Terraform | Infrastructure as Code with policy features | Widely adopted, relatively easy to use | Policy enforcement capabilities are somewhat limited |
| Conftest | Policy as Code tool for Kubernetes | Simple to use, integrates well with Kubernetes | Mostly focused on Kubernetes |
| Regula | Policy as Code for cloud infrastructure | Easy to use, supports multiple cloud providers | Might not be as customizable for very specific needs |
This table gives you a quick overview of some of the main players in the policy as code space, highlighting what they do best and where they might fall short. When choosing a tool, think carefully about what you need, what your team is comfortable with, and what your current infrastructure looks like.
Your Burning Questions Answered: Frequently Asked Questions about Policy as Code and OPA
To help clear up any confusion and answer some common questions, here are some FAQs about policy as code and OPA:
Policy as Code automates the governance and compliance of your code and how it runs. This makes sure everything follows your organization’s rules and any legal requirements. By automating security policies and immediately spotting any violations, it really helps improve cloud security.
By automatically checking and consistently enforcing policies about how data is stored, kept, and protected, Policy as Code helps you meet regulations like GDPR and PCI DSS, reducing the chances of compliance issues.
Besides Open Policy Agent (OPA) and HashiCorp Sentinel, other popular tools include AWS Config Rules, Terraform (which has some policy features), Conftest (for Kubernetes), and Regula (for cloud infrastructure).
Policy as Code makes sure that the way your cloud resources should be set up is defined and enforced through code. It constantly checks if the actual setup matches what you’ve defined, and can even automatically fix any differences.
You’ve got a few options: you can include user info in JSON Web Tokens (JWTs), set up OPA to regularly sync with LDAP/AD, or write OPA policies that directly query LDAP/AD when they need user information.
In Rego, you can have rules that both allow and deny something. It’s up to you, the policy writer, to decide which one takes precedence. Often, you’ll define a special document (like authz) where you set the logic for how to resolve these conflicts. You can also use the else keyword to give priority to certain rules.
Generally, no. The order in which you write your statements in Rego doesn’t usually change how the policy works. However, you can use the else keyword to make the order matter, allowing more specific rules to override more general ones based on their position.
Rego has a few: := for assigning values to local variables, == for comparing if two values are the same, and = which does both assignment and comparison. It’s generally best to use := for declaring variables and == for checking if things are equal whenever you can, as it makes your code easier to read and maintain.
OPA lets different teams write their policies in separate “packages.” Then, you can have a central policy that “imports” these team policies and combines their decisions, giving you a flexible way for everyone to contribute to the overall policy framework.
For situations where speed is critical, try to write policies that don’t involve a lot of looping or searching. Using objects instead of arrays when you have a unique identifier can help. Also, simple equality checks can improve performance by allowing OPA to index rules effectively. For more complex policies, you might look into “partial evaluation” to optimize them.
Rego is the special policy language that OPA uses. It’s designed specifically for working with structured data like JSON, making it easy to write policies for things like authorization, checking configurations, and filtering data.
Authentication is about verifying who a user is, while authorization is about determining what an authenticated user is allowed to do with specific resources. Policy as code with OPA is mainly focused on the authorization part.
Seeing is Believing: Real-World Success Stories of Policy as Code with OPA
Lots of organizations have successfully adopted policy as code with OPA to improve their security, compliance, and governance. Big names like Netflix and Pinterest, who were early adopters, even built their own custom systems to manage OPA at scale, showing how adaptable it is for large, complex environments.
OPA is being used in all sorts of different areas. In payment processing, it helps with fine-grained authorization based on things like how long an authorization is valid, the permission level, and details about the bank accounts and transaction amount. Banks and other financial institutions use OPA for role-based access control (RBAC), giving specific employees access to business bank accounts based on their roles and permissions. Even weather forecasting companies use OPA to manage who can access their APIs, controlling which third-party apps can get specific weather data based on various criteria.
Beyond just application-level access, OPA has been really helpful in making sure cloud environments are secure and compliant. Organizations use OPA to ensure their cloud infrastructure follows internal standards and regulatory requirements, like CIS benchmarks and SOC 2 compliance. When it comes to Kubernetes, OPA is widely used for admission control, enforcing policies about resource limits, which software sources are allowed, and preventing the use of risky “privileged” containers. OPA is also used for API authorization and making sure only necessary access is granted in microservices setups, ensuring that only authorized services can talk to each other. It’s even used as a control engine in CI/CD pipelines, checking configurations and compliance during the development process. These real-world examples show just how much of an impact policy as code with OPA is having across different kinds of technology.
Conclusion: Embracing Policy as Code with OPA for Robust Cloud Governance
In today’s fast-paced tech world, managing the growing complexity of cloud environments requires a more automated and reliable approach to policies. Policy as code, especially with the Open Policy Agent, offers a powerful way to tackle these challenges. By defining, managing, and enforcing policies through code, organizations can achieve new levels of automation, consistency, security, and compliance. OPA’s flexibility as a central policy engine, combined with the power of its Rego language, allows teams to implement detailed controls across their entire technology stack, from infrastructure as code to container orchestration and even application-level access. While getting started with policy as code and OPA might have a few bumps in the road, the long-term benefits of better governance, stronger security, and smoother compliance make it an essential tool for any organization aiming for solid cloud governance in the modern era. Adopting this way of thinking is no longer just a good idea; it’s becoming a must for navigating the complexities of the digital world with confidence and control.
References
- What is Policy as Code (PaC)? - CrowdStrike, accessed on April 6, 2025, https://www.crowdstrike.com/en-us/cybersecurity-101/cloud-security/policy-as-code/
- Policy as Code | Sentinel - HashiCorp Developer, accessed on April 6, 2025, https://developer.hashicorp.com/sentinel/docs/concepts/policy-as-code
- What is Policy as Code? - Permit.io, accessed on April 6, 2025, https://www.permit.io/blog/what-is-policy-as-code
- Documentation - Open Policy Agent, accessed on April 6, 2025, https://www.openpolicyagent.org/docs/latest/
- What is an Open Policy Agent (OPA)? - Sysdig, accessed on April 6, 2025, https://sysdig.com/learn-cloud-native/what-is-an-open-policy-agent-opa/
- Open Policy Agent (OPA) for Cloud Native Security - Styra, accessed on April 6, 2025, https://www.styra.com/open-policy-agent/
- 5 Use Cases for Using Open Policy Agent - Jit.io, accessed on April 6, 2025, https://www.jit.io/resources/security-standards/5-use-cases-for-using-open-policy-agent
- Understanding Open Policy Agent: A Simple Guide to OPA | by The kube guy | Medium, accessed on April 6, 2025, https://thekubeguy.com/understanding-open-policy-agent-a-simple-guide-to-opa-77aff7ff9819
- Terraform - Open Policy Agent, accessed on April 6, 2025, https://www.openpolicyagent.org/docs/latest/terraform/
- Kubernetes with Open Policy Agent (OPA) & Gatekeeper - Spacelift, accessed on April 6, 2025, https://spacelift.io/blog/opa-kubernetes
- The challenges of using OPA for application authorization - Aserto, accessed on April 6, 2025, https://www.aserto.com/blog/the-challenges-of-using-opa-for-application-authorization
- OPA Management: Challenges and Opportunities | Styra, accessed on April 6, 2025, https://www.styra.com/blog/opa-management-challenges-and-opportunities/
- Open Policy Agent Can Do THAT?! The Many Use Cases of OPA - YouTube, accessed on April 6, 2025, https://www.youtube.com/watch?v=phvSK4pW1K8