In today’s rapidly evolving digital landscape, security is paramount—especially in DevOps environments where CI/CD pipelines and cloud infrastructure drive software delivery. One paradigm that’s reshaping our approach to security is Zero Trust. This article explores Zero Trust in the context of DevOps pipelines, with a focus on practical AWS tools, IAM, VPC endpoints, and micro-segmentation strategies, all while ensuring that even complex security measures remain accessible and actionable.
What is Zero Trust and Why Should You Care?
Zero Trust is a security framework based on the principle: never trust, always verify. Unlike traditional security models that rely on a secure perimeter, Zero Trust assumes that every request—whether from inside or outside your network—must be authenticated and authorized.
Why Zero Trust Matters in DevOps:
- Dynamic Environments: Modern CI/CD pipelines and cloud infrastructures (like AWS) are dynamic. Zero Trust ensures every interaction is verified, no matter its origin.
- Enhanced Security: Through strict IAM policies and automated security rule checks, Zero Trust protects critical assets by limiting access to the minimum necessary.
- Minimized Risk: Techniques such as micro-segmentation in AWS environments limit lateral movement, reducing the damage potential in case of breaches.
How Does Zero Trust Fit into CI/CD Pipelines?
What Role Does Zero Trust Play in Your CI/CD Workflow?
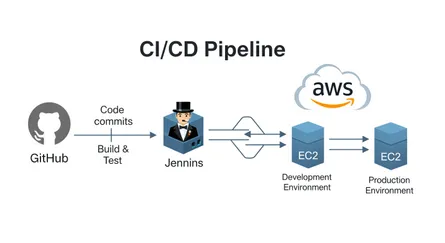
CI/CD pipelines automate the process of code building, testing, and deployment. Without robust security, vulnerabilities may creep into production. Zero Trust addresses this by:
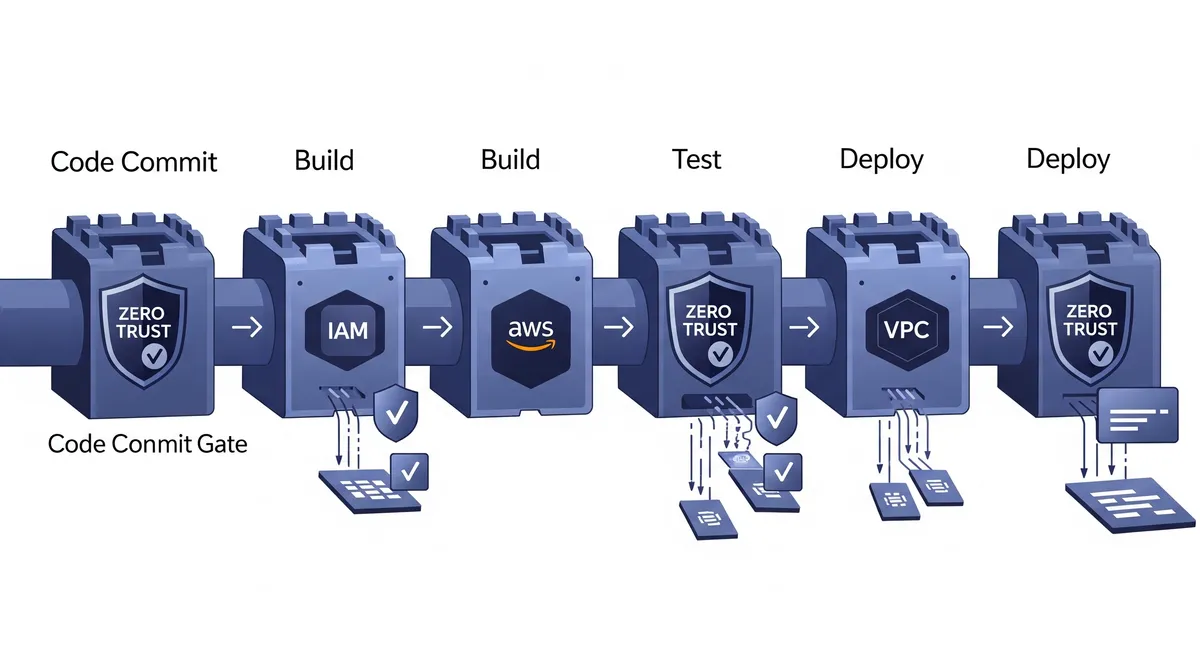
- Continuous Verification: Every step in the CI/CD pipeline—from code commit to deployment—undergoes stringent verification, forming a series of Zero Trust security gates.
- Least Privilege: Only essential permissions are granted. If an attacker compromises one segment, they won’t have unrestricted access.
- Automated Security Checks: Integrate automated scans and vulnerability assessments to catch issues before they escalate.
By applying Zero Trust principles, your CI/CD pipeline becomes a fortress where every request is authenticated, ensuring that only trusted code is deployed.
How Can You Implement Zero Trust in Your DevOps Pipeline?
What Are the Key Components for Zero Trust in DevOps?
Implementing Zero Trust involves a combination of tools, processes, and cultural shifts. Here’s how you can start:
1. AWS IAM for Granular Access Control
Use AWS-native Zero Trust tools such as IAM to enforce the principle of least privilege. Every user and service should have only the access they need.
2. VPC Endpoints for Secure Connectivity
Configure VPC endpoints to keep traffic between your VPC and AWS services private, ensuring data never traverses the public internet.
3. Micro-Segmentation in AWS Environments
Think of micro-segmentation as locking each room in a house rather than just the front door. It restricts lateral movement, so even if one segment is compromised, others remain secure.
4. Automated Security Rule Checks in CI/CD Pipelines
Integrate automated vulnerability scans (using tools like Snyk) into your pipeline to enforce continuous verification.
5. Zero Trust CI/CD Security Gates
Incorporate security checks at each stage of the pipeline—from code commit to deployment—ensuring that any anomaly is caught early.
What Are the Benefits of Adopting Zero Trust in DevOps?
How Does Zero Trust Enhance Security?
- Granular Access Control: Strict IAM policies ensure users and services have minimal access, reducing the potential attack surface.
- Reduced Attack Surface: VPC endpoints keep sensitive communications internal, shielding them from external threats.
- Continuous Monitoring: Automated security checks ensure vulnerabilities are detected and addressed quickly.
- Adaptive Authentication: Even if credentials are compromised, additional verification measures are in place.
Can Zero Trust Improve Efficiency?
Absolutely! Though adopting Zero Trust might seem complex initially, it streamlines your security processes over time:
- Faster Response Times: Automated policies enable quick remediation of vulnerabilities.
- Developer Confidence: With a secure pipeline, developers can focus on innovation rather than security concerns.
- Enhanced Compliance: Zero Trust makes it easier to meet regulatory requirements by enforcing strict access controls and maintaining audit logs.
Frequently Asked Questions (FAQs)
A: Zero Trust means treating every request as untrusted until it’s verified, regardless of its origin. It’s about continuous validation rather than assuming any part of your network is safe.
A: In DevOps, Zero Trust is applied at every pipeline stage. It enforces strict access controls using tools like AWS IAM, secures communication with VPC endpoints, and uses micro-segmentation to limit lateral movement.
A: No. While AWS provides excellent native tools for Zero Trust, the principles can be applied in any environment—cloud-based, on-premises, or hybrid.
A: Key tools include AWS IAM for managing permissions, VPC endpoints for secure connectivity, and automated security scanning tools like Snyk for vulnerability assessment.
A: By enforcing the principle of least privilege and continuously verifying access, even insiders only get limited permissions, making unauthorized actions easier to detect.
A: Start by gradually refactoring pipelines to integrate Zero Trust principles. Use API gateways to manage access to legacy systems, and adopt hybrid solutions like AWS Outposts to extend modern security practices to older environments.
Implementing Zero Trust in a CI/CD Pipeline: A Step-by-Step Guide
Step 1: Assess Your Current Environment
Begin by reviewing your existing CI/CD processes and infrastructure. Identify critical assets, the flow of sensitive data, and current access control mechanisms. Look for potential gaps where implicit trust may be present.
Step 2: Define Your Security Policies
Establish clear security policies that align with Zero Trust principles. Decide on the minimum access rights for each role and define rules for how each component in your pipeline should interact.
Step 3: Configure AWS IAM
For cloud environments, configure IAM policies to ensure each user or service has only the access they need. For example:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": "s3:ListBucket", "Resource": "arn:aws:s3:::your-bucket" }, { "Effect": "Allow", "Action": "s3:GetObject", "Resource": "arn:aws:s3:::your-bucket/*" } ]}This JSON policy limits access to a specific S3 bucket and is an example of applying the principle of least privilege.
Step 4: Secure Network Communication with VPC Endpoints
Configure VPC endpoints to ensure that traffic between your AWS resources stays within your private network. This reduces exposure to the public internet, thereby enhancing security:
# AWS CLI command to create a VPC endpoint for S3aws ec2 create-vpc-endpoint --vpc-id VPC_ID --service-name com.amazonaws.REGION.s3 --route-table-ids RTB_IDStep 5: Enforce Micro-Segmentation
Segment your network to isolate critical services. Use tools like security groups, network ACLs, or service meshes to ensure that communication between different parts of your pipeline is tightly controlled.
Step 6: Integrate Automated Security Checks into CI/CD
Incorporate automated scanning tools into your CI/CD pipeline. For example, use a tool like Snyk or Aqua Security to scan your container images or code for vulnerabilities before deployment.
Step 7: Continuous Monitoring and Logging
Implement continuous monitoring to track access and usage patterns. Tools like AWS CloudTrail, Prometheus, and ELK stack can help you collect logs and detect anomalies, ensuring that every action is audited and verified.
Zero Trust Best Practices for DevOps Pipelines
- Least Privilege: Always grant the minimum necessary permissions to every component in your pipeline.
- Multi-Factor Authentication (MFA): Require MFA for accessing critical systems.
- Automated Policy Enforcement: Use policy-as-code to automate the validation of your security configurations.
- Regular Audits: Perform periodic audits of IAM policies, network configurations, and access logs.
- Training and Awareness: Ensure that your team is aware of Zero Trust principles and follows secure practices.
Real-World Case Study: Implementing Zero Trust in a CI/CD Pipeline
Imagine a mid-sized software company that deploys applications on AWS using a CI/CD pipeline. Initially, the company operated under the assumption that their internal network was secure. However, after experiencing a breach due to compromised credentials, they decided to implement a Zero Trust model.
The Challenge
The company had a complex pipeline with multiple teams contributing code. Access control was loosely enforced, and once inside the network, attackers could move laterally without much resistance.
The Solution
They implemented a Zero Trust architecture by:
- Revising IAM policies to enforce the least privilege.
- Setting up VPC endpoints to restrict external traffic.
- Segmenting their network using micro-segmentation techniques.
- Integrating automated security scans into their CI/CD pipeline.
- Implementing MFA and continuous monitoring.
The Outcome
The result was a more secure, resilient, and auditable pipeline. The company saw a significant reduction in security incidents and increased confidence in their deployment process.
Avoid These Zero Trust Mistakes
Even with the best intentions, implementing Zero Trust can be challenging. Here are some common pitfalls and how to avoid them:
- Overcomplicating IAM Policies: Start with broader policies and gradually refine them rather than attempting overly granular rules from the start.
- Ignoring Third-Party Integrations: Extend Zero Trust principles to external tools by using API authentication and secure integration methods.
- Neglecting Legacy Systems: Integrate legacy systems gradually using API gateways and hybrid cloud solutions to avoid creating security gaps.
Conclusion
Zero Trust is more than a buzzword—it’s a paradigm shift essential for securing modern DevOps pipelines. By applying Zero Trust principles to your CI/CD process using AWS IAM, VPC endpoints, and micro-segmentation, you can significantly reduce risk and enhance security. With continuous verification and automated security checks, your environment becomes more resilient against both external and internal threats.
Start implementing Zero Trust today by assessing your current environment, defining strict security policies, and integrating these practices into your CI/CD pipelines. With the right tools and strategies, you can protect your cloud-native workflows and keep your organization secure.
References
- NIST Special Publication 800-207: Zero Trust Architecture.), https://csrc.nist.gov/publications/detail/sp/800-207/final
- AWS Well-Architected Framework - Security Pillar.), https://docs.aws.amazon.com/wellarchitected/latest/security-pillar/welcome.html
- AWS Identity and Access Management (IAM) Best Practices.), https://docs.aws.amazon.com/IAM/latest/UserGuide/best-practices.html
- VPC Endpoints and VPC Endpoint Services - Amazon Virtual Private Cloud.), https://docs.aws.amazon.com/vpc/latest/userguide/vpc-endpoints.html
- Implementing Microsegmentation with AWS Network Firewall.), https://aws.amazon.com/blogs/networking-and-content-delivery/implementing-microsegmentation-with-aws-network-firewall/
- Securing CI/CD Pipelines - Cloud Security Alliance.), https://cloudsecurityalliance.org/research/guidance/ (Note: Search for relevant CI/CD security documents on the CSA website)
- DevSecOps: Integrating Security into the DNA of Your DevOps Processes - SANS Institute.), https://www.sans.org/white-papers/ (Note: Search for relevant DevSecOps papers on the SANS website)
- Zero Trust for DevOps: A Practical Guide - (Example: Reputable Security Blog or Vendor Whitepaper, e.g., Palo Alto Networks, Zscaler, Okta.), [Link to a relevant resource]
- Automated Security Testing in CI/CD Pipelines - (Example: OWASP or a tool vendor like Snyk, Veracode.), [Link to a relevant resource]
- The Forrester Wave™: Zero Trust eXtended Ecosystem Platform Providers.), [Link to Forrester report summary if publicly available, or general Forrester site]
- Gartner: Market Guide for Zero Trust Network Access.), [Link to Gartner report summary if publicly available, or general Gartner site]
- Zero Trust Security Model - Microsoft Docs.), https://docs.microsoft.com/en-us/security/zero-trust/