Hey, so you know how keeping our tech stuff secure and following all the rules can be a real headache these days? With everything moving to the cloud and so many regulations popping up, it’s tough to keep track. That’s where compliance as code comes in, and it’s actually a pretty cool idea.
So, What’s the Deal with Compliance as Code?
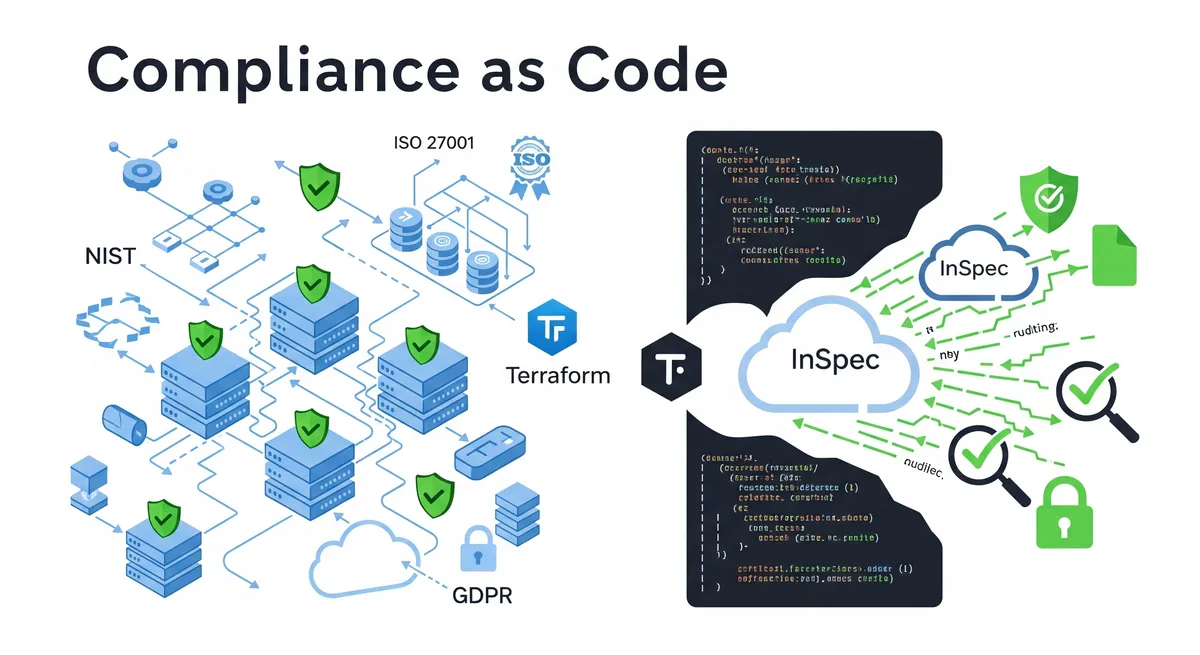
Think of compliance as code as baking security and rule-following right into how we build and run our software. Instead of just checking things at the end, we’re making sure everything’s up to snuff from the very beginning, almost like setting up guardrails in code. Basically, we’re turning those long lists of compliance rules into automated tests that our systems have to pass before they can go live. The whole point is to make sure we’re always meeting the necessary standards, both the ones from the government and the ones we set for ourselves. It’s about automating the whole compliance process, from setting things up to checking them, fixing issues, keeping an eye on things, and even creating reports. At the end of the day, compliance as code is all about making compliance a built-in, automatic part of our digital world.
This is a big step up from the old way of doing things, where we’d usually have manual checks every now and then. Instead of scrambling to fix problems right before an audit or after something goes wrong, compliance as code helps us be proactive and catch issues early on. This “shift left” approach means we can stop problems before they even happen, which saves us a ton of time and effort. Plus, it fits right in with the whole “everything as code” idea, where we’ve already seen how using code to manage our infrastructure (Terraform, anyone?) has been a game-changer. By bringing that same approach to compliance, we can use things like version control, automation, and teamwork to make sure we’re following the rules in a much smarter and more reliable way.
Why All the Fuss About Compliance These Days?
You might be wondering why compliance has become such a big deal. Well, there are a few key reasons.
First off, the rules are getting more and more complicated. There are tons of security standards and compliance rules out there, like SOC 2, ISO 27001, PCI DSS, HIPAA, GDPR, and NIST. These tell us how we need to operate legally and ethically, especially when it comes to keeping sensitive information safe and managing risks. Take the GDPR, for example, which has really strict rules about protecting the personal information of people in Europe. Or NIST frameworks, which are a must for US government agencies and anyone working with them. And then there’s ISO 27001, which is a standard recognized worldwide for setting up and managing information security. With so many rules, and sometimes they even overlap, trying to manage everything manually can get messy and lead to mistakes.
Second, cyberattacks are becoming more common and more sophisticated. It feels like we hear about a new one every week, right? That’s why it’s so important to have strong security measures in place. If our network security isn’t tight or if our cloud setups aren’t configured correctly, it can leave us wide open to attacks. Scary enough, a lot of data breaches happen because of misconfigured storage in the cloud, which just shows how crucial it is to have solid and consistent security controls. We really need to move beyond just reacting to attacks after they happen and start being proactive, with continuous monitoring and automated enforcement.
Finally, the consequences of not following the rules can be pretty serious. We’re talking big fines, legal trouble, and a damaged reputation that can be hard to recover from. Data breaches, in particular, don’t just cost us money right away; they can also make customers lose trust in us, which can hurt our business in the long run. For some standards, like ISO 27001, not staying compliant can even mean losing your certification, which can be a big deal for certain business opportunities. All these potential downsides really highlight why we need to use effective and automated ways to manage compliance and protect ourselves.
How NIST, ISO 27001, GDPR, and Compliance as Code Work Together
So, how do specific sets of rules like NIST, ISO 27001, and GDPR fit into this whole compliance as code picture?
The National Institute of Standards and Technology (NIST) has put together a really thorough set of guidelines and best practices to help organizations beef up their cybersecurity and handle risks effectively. If you’re a US federal government agency or a contractor working with them, you often have to comply with NIST frameworks. Because NIST guidelines are usually very detailed and specific, they’re perfect for turning into code. We can use tools like Terraform to translate those NIST security rules into infrastructure code, which means we can automate security checks and make sure our setups always meet NIST standards. Plus, tools like InSpec can automatically check if we’re still compliant, so we can be sure we’re always following the rules.
ISO 27001 is a standard that’s recognized around the world. It gives us a framework for setting up, putting in place, maintaining, and constantly improving an Information Security Management System (ISMS). It’s a comprehensive way to manage and protect all the sensitive information an organization has. Getting ISO 27001 certified can show everyone that you’re serious about security and can also help you meet other rules, like GDPR, HIPAA, and SOC 2. Setting up an ISMS that follows ISO 27001 gives you a solid base for meeting the data security requirements of the GDPR. The way ISO 27001 looks at risk and the detailed security measures it suggests can be really well implemented and checked using compliance as code. This gives us a systematic and automated way to handle information security, which lines up nicely with what the GDPR wants us to do.
The General Data Protection Regulation (GDPR) is a set of rules from the European Union that’s all about protecting people’s data and privacy within the EU. And it doesn’t just apply to companies in Europe; if you’re dealing with the personal data of anyone in the EU, you’ve got to follow these rules. The GDPR says that organizations need to have good technical and organizational measures in place to make sure the personal data they handle is secure and protected. Like we talked about, ISO 27001 is a great framework for meeting those technical and operational needs for GDPR compliance. And what’s really cool is that tools like InSpec are perfect for automatically checking if our systems meet the specific technical requirements of the GDPR, so we can keep an eye on our compliance all the time. The main idea behind the GDPR, which is “privacy by design,” fits perfectly with the proactive nature of compliance as code. It lets us build privacy and security into our systems and processes right from the start and constantly check if we’re still meeting the GDPR’s tough standards.
| Framework | Origin/Scope | Key Focus Areas | Relevance to Compliance as Code |
|---|---|---|---|
| NIST | US Federal Government & Contractors | Cybersecurity Framework, Risk Management | Detailed guidelines can be turned into code and enforced using Terraform and checked with InSpec. |
| ISO 27001 | International Standard | Information Security Management System (ISMS) | Risk-based controls can be set up with Terraform and checked for effectiveness with InSpec. |
| GDPR | European Union | Data Protection and Privacy | Technical requirements can be turned into InSpec checks and infrastructure managed by Terraform. |
Terraform and InSpec: The Power Duo for Compliance as Code
Two really helpful tools that make compliance as code possible are Terraform and InSpec.
Terraform is a popular open-source tool that lets us define and manage our infrastructure using code, whether it’s on different cloud providers or our own servers. It’s super useful for compliance as code because it lets us put our governance rules right into our infrastructure setup, making sure they’re applied consistently everywhere. Terraform helps us enforce security rules at the infrastructure level, like setting up secure storage, putting in place strong network controls, and managing who has access to what. Because it works so well with CI/CD pipelines, we can make sure our security and compliance rules are followed even before we deploy anything to production. Plus, it can connect with services like AWS Config to continuously monitor for any changes in our setup. Basically, Terraform gives us the foundation for compliance as code by letting us define how we want our infrastructure to look, including all the security and compliance bits, in a way that’s version-controlled, repeatable, and easy to audit.
InSpec, on the other hand, is an open-source tool specifically designed for automatically testing the security and compliance of our infrastructure, applications, and other tech stuff. It lets security and compliance teams write down their rules and requirements in a way that’s easy for humans to read, which makes it simpler to turn those regulatory standards into tests that can actually be run. We can use InSpec to check the infrastructure that Terraform sets up, making sure that what we’ve actually got matches the compliant setup we defined in our Terraform code. It’s like the “test” part of the equation, making sure that everything Terraform and other tools deploy follows the security and compliance standards we need. InSpec gives us the continuous checking and validation we need to keep our environment compliant.
| Feature | Terraform | InSpec | How it Enables Compliance as Code |
|---|---|---|---|
| Infrastructure Provisioning | Defines and deploys infrastructure as code using a declarative language. | N/A | Ensures infrastructure is set up in a way that meets our compliance needs. |
| Compliance Testing | Primarily focuses on infrastructure setup. Can work with policy tools. | Specifically designed for automated security and compliance testing of infrastructure and applications. | Checks that the infrastructure and applications we’ve set up meet our compliance rules and regulatory requirements. |
| Policy Enforcement | Can be extended with policy as code tools like Sentinel and OPA. | Can define compliance rules as code that can be run automatically. | Allows us to both prevent issues (Terraform with policy tools) and detect them (InSpec) to make sure we’re compliant. |
| Reporting | Shows us the state of our infrastructure. | Creates detailed reports on the results of our compliance checks. | Gives us proof that we’re compliant, both for ourselves and for when we have to show it to others during audits. |
Putting Compliance into Practice for NIST, ISO 27001, and GDPR with Terraform
To really make compliance as code work for NIST, ISO 27001, and GDPR using Terraform, there are a few important things we need to do.
First, we’ve got to carefully translate the specific technical rules and requirements of these frameworks into actual Terraform code. This means really understanding each framework and how its rules apply to the settings and configurations of our cloud resources. For example, if NIST says we need to encrypt our data, we can use Terraform to make sure that services like S3 buckets and databases are always encrypted. Similarly, for GDPR, our Terraform code can make sure that all personal data, whether it’s being stored or moved around, is encrypted using strong methods and that only the right people have access. To align with ISO 27001’s focus on who can access what and keeping logs, we can use Terraform to set up detailed access rules, configure logging for all sorts of resources, and divide our network into secure sections. It’s super important to get this translation right, turning those sometimes abstract compliance rules into the specific settings that Terraform can manage. This often means that the people who know the compliance stuff need to work closely with the engineers who know Terraform.
Second, it’s a good idea to use reusable Terraform modules as much as possible. This helps make sure everything is consistent and reduces the chance of mistakes in our setup. These modules are like pre-approved, compliant building blocks that we can use across different projects and environments, so we know we’re always meeting our compliance standards. For instance, we could have a module for creating a virtual machine in AWS that’s already set up with the right security rules, access permissions, and encryption settings. Using these well-defined and compliant Terraform modules helps us keep things standard across our organization, making it easier to manage and maintain compliance as we grow, and it also helps us avoid human errors in our configurations.
Finally, adding Policy as Code tools to Terraform gives us even more control and automation. Tools like HashiCorp Sentinel or Open Policy Agent (OPA) let us define and enforce really specific rules on our Terraform setups. These rules can check for anything that might violate our organizational standards or regulatory requirements before we even set up the infrastructure, acting like preventative measures. For example, we could have a Sentinel policy that stops us from creating an S3 bucket if it doesn’t have encryption turned on, or that limits the types of virtual machines we can use to only those that meet our security needs. Policy as Code tools give us an extra layer of control and automation, letting us enforce complex compliance rules that go beyond what Terraform can do on its own, making sure that only compliant infrastructure ever gets deployed.
Automated Compliance Audits with InSpec: Keeping Things in Check
InSpec is key to making sure we have continuous governance through automated compliance audits.
One of the main things it does is check the infrastructure that Terraform has set up. It does this by running InSpec tests (also called controls) that look at the configuration and status of our cloud resources and compare them to the specific rules of NIST, ISO 27001, and GDPR. For example, an InSpec test can check if an AWS security group created by Terraform has the right incoming and outgoing traffic rules, according to our security policy. Similarly, InSpec can make sure that a database we set up with Terraform is encrypted when it’s not being used, that logging is turned on, and that the right people have access. These InSpec tests act like automated audits, constantly looking at our deployed infrastructure to confirm that it’s following the security and compliance standards we’ve set and that the regulations require.
To really keep things in check, we should put these InSpec tests right into our CI/CD pipelines. This way, every time we make a change to our infrastructure, it automatically gets checked for compliance before it goes live. If an InSpec test fails during this process, it means the change we’re trying to make would break a compliance rule, and the deployment can be stopped automatically. This prevents any non-compliant resources from ever making it to our production environment. This creates a “compliance gate,” making sure that only infrastructure that meets our security and regulatory standards can be deployed, which moves our compliance checks even earlier in the development process.
On top of that, InSpec can create detailed and easy-to-read reports that summarize the results of our compliance audits. These reports clearly show which tests (controls) passed and which ones failed, giving us a clear picture of our compliance status. These reports are really valuable for our internal teams, management, and even external audits, because they provide evidence that we’re following the security and compliance standards we need to. The reporting features of InSpec make the audit process much easier by giving us readily available and comprehensive documentation of our compliance checks, making it simpler to show that we’re meeting regulations and our own internal policies.
The Real Benefits of Using Compliance as Code
There are a lot of real advantages to using compliance as code.
First off, it makes our security stronger. By finding and fixing security weaknesses and compliance issues early on, we can stop them from ever reaching our live systems. Making sure our security rules are consistently applied across all our infrastructure reduces the chance of mistakes and human errors. Ultimately, by building security checks into our infrastructure and development processes, we significantly lower the risk of data breaches and security problems.
Second, it helps us meet regulations better. Automated checks make sure we’re constantly following the specific technical rules of frameworks like NIST, ISO 27001, and GDPR, which means we’re less likely to be non-compliant. Audits become much simpler and less disruptive because we have automated proof of our compliance ready to go. By consistently meeting regulatory requirements, we can avoid those big fines and legal issues that come with non-compliance.
Third, compliance as code makes us more efficient and agile. Automation really cuts down on the manual work involved in checking compliance, doing audits, and fixing problems, which frees up our IT teams to do other important things. Compliance issues get found and fixed much faster with automated checks, so we don’t have as many delays in our development and deployment processes. By giving developers built-in compliance guidelines, it lets them move faster and be more innovative without worrying about breaking security or regulatory rules.
Finally, it saves us money. Automating compliance processes means we don’t need as many people on dedicated compliance teams, which can lead to significant savings. By proactively preventing data breaches and security incidents, we avoid the big financial losses that come with those events, including fines, recovery costs, and damage to our reputation. And the improved efficiency from automation and less rework also helps us save money overall.
Things to Keep in Mind When Using Compliance as Code
Even though compliance as code has a lot of great benefits, there are some challenges to think about.
One big thing is the change in how people work together. Using compliance as code often means that development, security, and compliance teams need to change their mindsets and how they do things, and that can be tough if it’s not managed well. Organizations that aren’t used to agile and automation might find this transition especially hard. For it to work, there needs to be good teamwork and everyone needs to understand their role in compliance.
Another thing is the initial setup and how complex it can be. Figuring out all the governance rules and then turning them into code that actually works can take a lot of time and effort. It also requires people who really understand the compliance frameworks and who are good at using the automation tools like Terraform and InSpec. Teams might also need some time to learn how to use these new tools and frameworks. The initial investment in time, resources, and expertise to get a good compliance as code system up and running can be significant, so it’s something to plan for.
Also, there are some things that just can’t be fully automated. While compliance as code can handle a lot of the technical parts of compliance, some rules, especially those that need a human to make a judgment or involve manual steps, might be hard or impossible to automate completely. We might still need a mix of automated checks and manual reviews to make sure we’re fully compliant.
Lastly, good data management is key. We need to make sure that the data we use for our automated compliance checks is available, accurate, and reliable for compliance as code to work well. Organizations also need to be careful about managing sensitive information, like passwords and API keys, that might be used in Terraform files and InSpec tests to avoid security risks.
Compliance as Code in a Bigger Governance Plan
Compliance as code is a really important part of a bigger idea called Governance as Code. Governance as Code takes the ideas of compliance as code and applies them to a wider range of organizational rules, including security, who can access what, data privacy, how much things cost, and how we operate. It’s about defining and enforcing all these rules using automation and code, so we don’t have to rely as much on manual processes and we can make sure things are consistent across our IT infrastructure.
Policy as Code is what makes both compliance as code and Governance as Code possible. It’s about representing our rules and standards as code that can be automatically checked and enforced. When it comes to compliance, Policy as Code lets us turn our compliance requirements into code, so we can automatically find any violations and make sure our cloud resources and applications are meeting the necessary standards.
Compliance as code also helps us with continuous monitoring and improvement. It lets us constantly watch our infrastructure and applications to make sure they’re following our compliance rules, giving us real-time information about our compliance status. This continuous monitoring helps us catch any changes that might make us non-compliant early on, so we can fix them before they cause security problems or make us fail an audit.
Frequently Asked Questions About Compliance as Code with Terraform and InSpec
- Writing down compliance rules and security policies as code using a clear language.
- Automatically checking if our infrastructure and applications follow these rules.
- Putting these compliance checks right into our software development and deployment process.
- Constantly watching and giving us updates on the compliance status of our tech resources.
- ISO 27001 gives us a strong framework for setting up an Information Security Management System (ISMS), which covers a lot of the technical and organizational things we need to do for GDPR to protect personal data.
- The way it looks at risk helps organizations find and deal with risks to personal data, which is what GDPR wants us to do.
- Getting certified in ISO 27001 can show that we’ve taken the right security steps to meet GDPR’s data security rules
- Terraform lets us write down NIST security guidelines as code in our infrastructure setups.
- By using Terraform’s language, we can say exactly how we want our infrastructure to be set up to meet NIST standards.
- We can say exactly how we want our infrastructure to be set up to meet NIST standards.
- Connecting it with policy tools like Sentinel lets us check if we’re meeting NIST rules even before we deploy anything.
- We can also use Terraform to set up specific security settings that NIST recommends for different cloud resources, like encryption, access controls, and logging.
- InSpec lets security and compliance teams turn the technical rules of GDPR into code that can be run automatically (InSpec controls).
- These controls can then be run against our systems and infrastructure to check if they’re meeting GDPR’s data protection standards.
- By putting InSpec into our CI/CD pipelines, we can make sure our systems are constantly being checked against GDPR rules.
- InSpec gives us detailed reports on our compliance status, pointing out anything that doesn’t meet GDPR’s technical requirements.
- It makes our compliance practices more consistent and standard across the whole organization.
- It’s easier to scale our compliance efforts as our infrastructure grows.
- We can save a lot of money by automating things and reducing manual work.
- It helps us keep up with compliance rules that change often.
- It improves teamwork and understanding between development, security, and compliance teams.
- It gives us continuous monitoring and enforcement of compliance, making our security stronger.
- It makes delivering software faster and more efficiently by building compliance into the development process.
- Audits become simpler because we have automated ways to collect evidence and create reports.
- People might not like changing to new agile and automation ways of working.
- It can be hard to figure out and write down all the compliance rules accurately as code.
- Some compliance rules that need human judgment can’t be fully automated.
- We need people who know both the compliance rules and the automation tools (Terraform, InSpec).
- We need to manage and protect sensitive information used in our automation processes carefully.
- Chef’s blog has some good examples of how to use InSpec to check if infrastructure set up by Terraform is compliant, especially in AWS.
- The official documentation and community forums for Terraform and InSpec often have practical examples and ways to use them for Compliance as Code.
- You can often find examples of Terraform modules and InSpec profiles for specific compliance standards on platforms like GitHub.
Wrapping Up: Looking Ahead with Compliance as Code
Compliance as code is a really important step forward in how organizations handle the complexities of security and following the rules in today’s digital world. By building security and compliance checks right into our infrastructure and development processes, we can be more proactive, efficient, and reliable in how we govern ourselves. Tools like Terraform and InSpec give us the power to define, deploy, and constantly check our compliance with important frameworks like NIST, ISO 27001, and GDPR. While there might be some hurdles in getting started with compliance as code, the big benefits it offers in terms of better security, improved compliance, increased efficiency, and cost savings make it a must-have for organizations navigating the cloud era. Embracing compliance as code isn’t just a tech trend; it’s a fundamental shift towards a more automated, proactive, and ultimately more secure and compliant way of running our digital operations.
References
- Compliance as Code: Tutorial + Best Practices - Drata, accessed on May 16, 2025, https://drata.com/grc-central/compliance-as-code/what-is-cac
- What is Compliance as Code? The Best Way to Automate … - Puppet, accessed on May 16, 2025, https://www.puppet.com/blog/compliance-as-code
- Compliance as code | Thoughtworks United States, accessed on May 16, 2025, https://www.thoughtworks.com/en-us/insights/decoder/c/compliance-as-code
- What Is Compliance as Code? Benefits, Use Cases and Tools …, accessed on May 16, 2025, https://www.contino.io/insights/compliance-as-code
- Compliance Made Simple with Terraform | ControlMonkey, accessed on May 16, 2025, https://controlmonkey.io/blog/compliance-made-simple-with-terraform-cloud-governess/
- Using InSpec to DevOps GDPR compliance - Joe Gardiner, accessed on May 16, 2025, https://grdnr.io/post/2017-08-12-using-inspec-to-devops-gdpr-compliance/
- ISO 27001 and Privacy - IT Governance USA, accessed on May 16, 2025, https://www.itgovernanceusa.com/cyber-security-solutions/iso27001/iso27001_privacy
- ISO 27001 vs. NIST 800-53: Key Differences and Similarities - Security Compass, accessed on May 16, 2025, https://www.securitycompass.com/blog/iso-27001-vs-nist-800-53/
- What is Cloud Compliance? Standards, Solutions & More - Spacelift, accessed on May 16, 2025, https://spacelift.io/blog/cloud-compliance
- Terraform-Driven Compliance Audits: Enforcing Continuous Cloud Governance in AWS -, accessed on May 16, 2025, https://www.cycloid.io/terraform-driven-compliance-audits-enforcing-continuous-cloud-governance-in-aws/
- Infrastructure Testing and Compliance with Chef and Terraform, accessed on May 16, 2025, https://www.chef.io/blog/infrastructure-testing-and-compliance-with-chef-and-terraform
- Policy as Code Approach: How to Streamline Cloud Governance - EPAM SolutionsHub, accessed on May 16, 2025, https://solutionshub.epam.com/blog/post/policy-as-code
- What is Governance as Code? | Harness, accessed on May 16, 2025, https://www.harness.io/harness-devops-academy/what-is-governance-as-code
- GDPR Compliance Audit Software Solutions | Chef, accessed on May 16, 2025, https://www.chef.io/solutions/compliance/gdpr
- Sensitive data Classification for HIPAA,PCI DSS, GDPR, ISO 27001 ,CCPA and More., accessed on May 16, 2025, https://www.strac.io/blog/sensitive-data-classification-for-hipaa-pci-dss-gdpr-iso-27001-ccpa-and-more